Storing passwords in plaintext is inexcusable. Sadly, this practice is very common particularly among small websites. According to the hacker who broke into RockYou.com some years ago and stole 32 million passwords, 30% of websites store plain text passwords. The usual line of thinking is that their website is too small and obscure for anybody to hack, or that their users are unimportant and low-value. But they totally ignore the fact that users often reuse passwords. Even if a website’s user accounts have no value in the context of the information they hold, the user’s login credentials are valuable. And the hackers know it, which is precisely why they target small, obscure websites because their developers think exactly that. Small sites follow poor security practices and consequently when they get hacked and the password database stolen, the attacker gets away not just with the users’ logins on the site but logins on Facebook, GMail, Paypal and their bank accounts.
While you can't control how a website stores your password, you can control what services you sign up for. Stay away from websites that stores your password in plain text. A better practice will be to use a different username-password combination for every website you sign up on. Remembering so many passwords is hard, and this is where password manager like KeepPass and LastPass comes in.
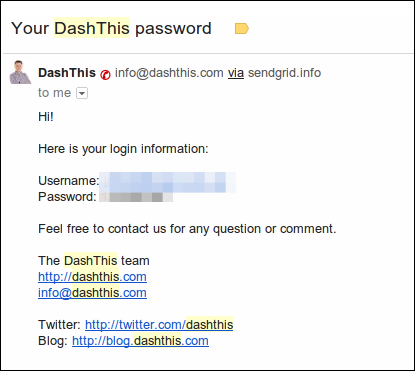
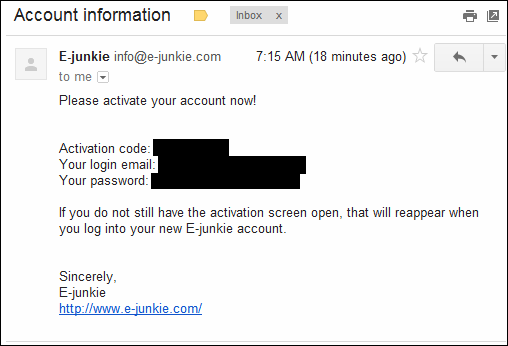
A good way to find out if a website stores your password in plaintext is to click the "forgot password" link. If the website sends you your password in an email, it means that they are storing the password itself and not the hash.
At PlainTextOffenders.com, you can browse hundreds upon hundreds of websites that exhibit a complete lack of regard for customer password security. Of course, the collection represents only a small fraction of websites that follow sloppy password security.
We’re tired of websites abusing our trust and storing our passwords in plain text, exposing us to danger. Here we put websites we believe to be practicing this to shame.
Regrettably, plaintextoffenders.com is not easy to browse. The website has a search function but it’s broken. The site itself is a simple Tumblr blog that hosts user submitted screenshots of password-reset email they received from the service with their passwords in plain sight. A better implementation of the same idea is at PasswordFail.com. They even have a Chrome extension that warn users when they visit a website that stores password in clear text. But their database is small.
If you happen to come across a service that emails you the password in clear text, take a screenshot, redact your personal information and submit it to the Plain Text Offender’s Hall of Shame. I encourage you to contribute to passwordfail.com as well. And don’t forget to notify the webmaster about their poor password security.
Photo credit: Big Stock Photo
[via Krebsonsecurity]
No comments:
Post a Comment